Idle Authentication application to make the most of your out-of-support Win PC, Source Code Release
Google Authentication System-like application that runs on Windows Win95 to Win11 with just one 152KB exe file
IdleAuthプロジェクト
The IdleAuth Project has released the executable for IdleAuth, an authentication application for Windows, for the first time on February 5, 2025 and the source code on April 11, 2025. It can be downloaded from the following URL
https://note.com/spinlock/n/n2e128e076798
Idle Authentication Application
What is the IdleAuth application?
It is something like an OTP where you enter alphanumeric characters displayed on the screen into a browser to verify your identity and make bank transfers. You need to enter random numbers sent from a website, but it works even on very old PCs. This is a great use for Windows 10 and earlier Windows PCs that no longer have Internet access. The safety of using the Idle Authentication App depends on the user's ability to use it. It is only available on websites that support the Idle Authentication application.
■You can create a system using authentication for free.
The specifications for the website side that supports the Idle Authentication App are publicly available. Many websites, such as two-step authentication for websites that use membership registration, can take advantage of the offline authentication characteristics of the Idle Authentication app to provide security that other authentication methods cannot. The source code of the application is publicly available so that users can verify that the application is secure. Also, since it is a single 152KB executable file, it is very convenient to verify safety through disassembly analysis. The output results of disassembly using debugging information output at compile time are also available, making analysis easy. For this reason, it may be more convenient than general open source.
■No hardware required for authentication
Since the entire PC on which the idle authentication application is installed is used as authentication hardware, the software alone can be used. However, the use of authentication hardware makes it even more secure: USB authentication keys and Smart card that support the conventional Windows Crypto API that have been around since the Win95 era can also be used. However, there is a possibility that certain hardware will not work in the future.
If Smart card and other devices are developed for idle authentication applications in the future, this is a very effective use of state-of-the-art semiconductors. Worldwide, the benefit will be realized. The effect of the hard error detection function that makes this benefit possible is tremendous. In the future, this could affect the cost of manufacturing internet-only credit cards and transportation smart card. The widespread use of idle authentication applications will provide even greater benefits.
One application for cutting-edge semiconductors is NPUs for edge AI. I think the direction is to reduce manufacturing of semiconductors that are less necessary and to reduce pollution. NPUs in particular are not only power-hungry to manufacture, but also power-hungry to use, and it would be good to reduce the number of NPUs by researching AI algorithms and linking them to servers, except for those applications where NPUs are absolutely useful. Just as the dedicated arithmetic unit of the RSA cipher was once reduced by the elliptic curve cryptography algorithm, which is computationally inexpensive. In other words, the direction of Smard card would be better for the world economy and the global environment than NPU for less necessary applications.
■Free forever!
We will not charge for idle authentication applications. There is a possibility that it may not work in the future due to Windows version upgrades. However, the source code we are releasing can be built with the latest version of Microsoft Visual Studio 2022. MFC is required to build the source code; MFC is included with Visual Studio 2022.(Builds are also possible for ARM and other non-x86 CPUs.)
Supported OS
Windows 95/98/98SE/ME
Windows NT4/2000/XP/Vista/7/8/8.1/10/11
Internet Explorer 5 or higher is required for 9X series and pre-2000 Legacy Windows.
(5.5 or higher is required to use the PfxOnly application separately.)
Since it is written in English, Windows of various languages other than Japanese Windows also presumably works.
■Very resistant to PC hardware failure.
Even PCs that are treated as junk due to some defects can be used if they work, to put it extremely simply. However, if a hardware error is detected or an authentication error occurs on the server side, please stop using the system immediately. Even if an authentication error was detected on the server side, there are very few cases of damage; even a 30-year-old Windows 95 machine can be used effectively. It may also be possible to make effective use of PCs whose prices have plummeted due to reputational damage; IdleAuth do not use the PC's internal clock, so even if the button battery on the motherboard is dead, IdleAuth will still work if they are booted up. Idle Authentication application is the strongest application against failures.
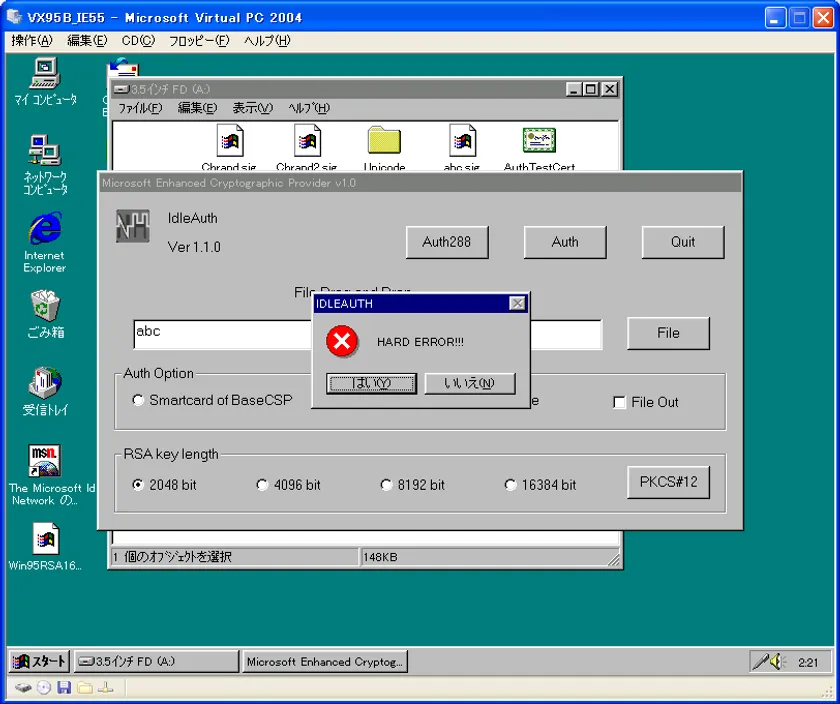
Hardware Error Detection Screen
■Hard Error Detection Function
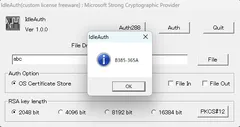
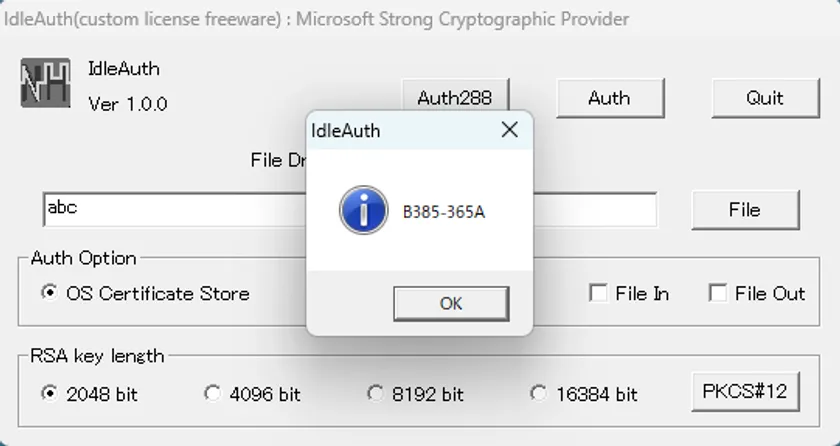
The result of the RSA cryptographic signature operation is compressed into 4 bytes and displayed in 8 hexadecimal digits. Idle authentication applications detect hard errors by verifying the results of signature operations with RSA cryptography. Unlike parity, errors are reliably detected. Even in the unlikely event that the verification operation is a false operation, the server can handle it appropriately. (Please process).
Digital certificate issuing function for applications
Idle authentication applications can issue RSA 2048/4096/8192/16384-bit digital certificates. By using the auxiliary tool PfxOnly, it is possible to operate without leaking the value of the public key. For this reason, RSA 2048-bit is secure, but 4096 (8192) bit or more is recommended in case of leakage.
For your information, RSA encryption has a risk of being deciphered by a quantum computer. However, by making the value of the public key invisible, it is now expected to be the most stable public key cryptosystem in the world, which is why it is gaining in importance. Strictly speaking, this means that it can replace some of the uses of public key cryptography rather than public key cryptography. We call this new cipher Invisible RSA (Shadow RSA).
■ Website
Idol Authentication Application Official Website
https://icanal.idletime.tokyo/idleauth/
Auxiliary tool PfxOnly (only if required by the system)
- Category:
- Services